Potential Okta system compromise by Lapsus$ group came out this week. Okta, a leading provider of authentication services and Identity and access management (IAM) solutions, has announced that it is investigating data breach suspicions.
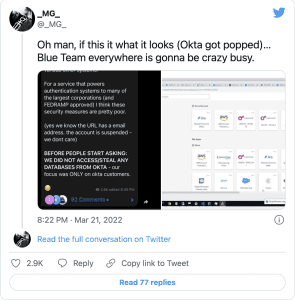
On Tuesday, the data extortion group Lapsus$ shared screenshots of what it claims is access to Okta’s backend administrative terminals and customer data in their Telegram channel.
Okta, a publicly traded firm with a market cap of more than $6 billion, employs over 5,000 people worldwide and provides identity management and authentication services to large corporations such as Siemens, ITV, Pret a Manger, and Starling Bank, among several others.
Lapsus$ alleges Okta customer data breech
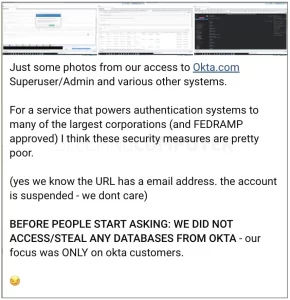
The screenshots by Lapsus$ claim that they have access to Okta Superuser/Admin systems. They also claim that their only interest is in the customer data, which is very concerning.
“Okta is aware of the reports and is presently investigating,” a representative for the company informed BleepingComputer.
“As additional information becomes available, we will offer updates.”
Screenshots released by Lapsus$, as seen by BleepingComputer, show the system date set to January 21st, 2022, implying that the hack occurred months ago.
One of the screenshots demonstrating Lapsus$”superuser’ access to Okta’s admin console also displays a URL with an email address belonging to a presumably compromised Okta customer support person.
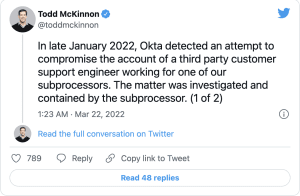
Todd McKinnon, co-founder and CEO of Okta, has now confirmed this:
“We believe the screenshots that were online relate to this January event,” McKinnon adds.
“Based on our findings thus far, there is no evidence of ongoing malicious behavior beyond the activity observed in January.”
However, one of the screenshots shared suggests that Lapsus$ may alter client passwords through Okta’s admin panel.
Security analysts are concerned that the hacker organization may have utilized this ‘superuser’ access to compromise the servers of customers.
Lapsus$ bolstered this notion by claiming that they did not attack Okta to steal the company’s databases, but rather to target their consumers.
“BEFORE PEOPLE START ASKING: WE DIDN’T ACCESS/STEAL ANY DATABASES FROM OKTA – our emphasis was ONLY on okta customers,” Lapsus$ said in a Telegram thread.
With numerous well-known organizations employing Okta, including Fedex, Peloton, SONOS, T-Mobile and JetBlue, this is obviously a major worry.
This is a stream of hacks by Lapsus$ Group
The news comes on the heels of Lapsus$’ accusations that it hacked Microsoft’s internal Azure DevOps server.
On Monday, Lapsus$ claimed to have leaked 37 GB of stolen source code for Bing, Cortana, and other Microsoft projects. Microsoft stated that it was looking into it.
Furthermore, the organization announced today that it has infiltrated LG Electronics (LGE) for the “second time” in a year.
Lapsus$ has previously disclosed gigabytes of confidential material reportedly stolen from major corporations. This list includes Samsung, NVIDIA, and Mercado Libre, which revealed a compromise this month.
Material extortion gangs like Lapsus$ take and keep victims’ proprietary data. Which they then disseminate if their extortion demands are not satisfied.
If Lapsus$’ allegations are true, the public needs to know how many of Okta’s clients were affected. Okta System compromise by Lapsus$ is something everyone should be aware of.