It’s true, someone created a technique of phishing passwords that doesn’t rely on the usual telltale signs. What’s worse, its tricking even the most experienced users.
Let’s get into it.
New Phishing Technique?
The new technique in question is called BitB, which is short for “browser in the browser.”
Basically, a fake browser page, spoofing a normally trust worthy browser, an OAuth (Open Authorization) page. The phony browser page hides within the trusted browser window and goes undetected.
Thousands of websites employ OAuth protocol to allow their users access to existing accounts. Think about every time you login somewhere, it usually prompts you to use Google, Facebook or Apple to quickly sign in.
In theory, this login method is supposed to lessen the time it takes to make a new account by giving the option to use an existing account. The OAuth page then takes care of the rest of the process.
How this Technique Tricking Users
Simply put, BitB exploits users’s trust in these processes.
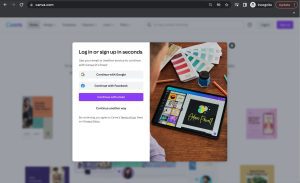
Take Canva for example. This content editing platform allows users to login using any of the three common accounts: Google, Facebook or Apple.
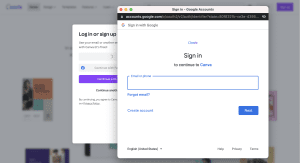
Let’s say you choose to login with Google. After you click “Sign in with Google”, a new browser window will open up for you to type in your Google credentials.
The problem is, if you don’t pay close enough attention, you won’t be able to notice a phishing attempt already in progress. As a user, you are expecting these windows to pop-up, and that it’s reliable.
The OAuth protocol is meant to be a secure method of ensuring that only Google receives your password. Websites like Canva, never see this information. OAuth holds a secure login session with Google, and then when everything checks out, Google provides the user with a token that gains access to Canva.
You’ve probably seen this when using PayPal to pay at checkout from basically any site.
You’ve probably become so accustomed to this method that you trust it whole heartedly.
Where BitB Takes Advantage
Instead of having a legitimate second browser window pop up that really connects to Google or PayPal’s servers, BitB uses a series of HTML and CSS to spoof the appearance of legitimacy.
Even the URL they display to you will appear valid. They are doing everything they can to make you think this second browser window checks out. In most cases, the windows are identical.
A researcher with the handle mr.d0x describes this technique. His proof-of-concept effort begins with a Web page that features a painstakingly accurate replica of Canva.
If a visitor chooses to log in with Apple, Google, or Facebook, the phony Canva page redirects to a new page embedded with what appears to be the familiar-looking OAuth page.
This new page is a spoof as well. It has all of the graphics one would expect to see when logging in with Google. The new window functions similarly to a browser window of a real Google OAuth page.
A fake within a fake.
How it works
The reality is the fake Canva site never opens a new window. It only makes it look like it did.
The HTML and CSS have the appearance of a second page layering on top on the website page.
If you fall for this scheme you will literally type in your Google credentials into this “login”. These bad actors will now have access to your Google account, and every website you use Google to login to.
This new BitB technique is surprisingly simple and effective.
Even highly experienced tech experts can fall for this trick if they have a quick lapse of judgement. That’s how believable these pages are.
Phishing is Tricky to Spot, but Not Impossible
There is some good news in all this. Although this phishing technique tricking experts can be extremely convincing, it does have flaws.
This method has a few weaknesses that gives us tech folk a way to detect it:
Remember that authentic OAuth pages (or payment windows) are separate windows. You should be able to move them around with your mouse and drag them just about anywhere. Specifically, you can drag them above the address bar on the primary window.
The BitB windows on the other hand, does not have this dragging capability.
By contrast, the pop-up isn’t a second window at all. Even if you are able to move around the illusion created by HTML and CSS, you will never be able to move it above the primary address bar because they are directly on the primary page.
It seems like an easy solution, but that’s only because you have been made aware of it. In real time, normal users don’t think information is being stolen every time they sign into a different website or payment system.
Checking for phishing is telling you and other users to do something they never do.
For bad actors, they only need you to slip up once. Everything can be fine for 50 logins, so you stop checking and on login 52, your information is stolen.
What You Can Do
This is why I always stress to my clients the use of two-factor authentication. It is the easiest way to protect your accounts.
For those with a little more experience, I would suggest right clicking on the “pop-up” page and choose “inspect.” If the window is a Bitb page, the URL will be hardcoded in the HTML.
Overall, this new phishing technique tricking experts is something we as internet users should all be aware of. Knowledge is power, and awareness is key.
Check out this blog on ways to avoid falling victim to phishing attacks.
If you are looking for some two-factor authentication options, we would love to give you a recommendation. Feel free to book a time to chat with us via the Calendly link below. I’d be happy to discuss ways to optimize your company’s IT
Click here to schedule a free 15-minute meeting with Stan Kats, our Founder and Chief Technologist.
STG IT Consulting Group proudly provides IT Service for Small to Medium Businesses in Greater Los Angeles. We’d love to see if we can help you too!